It’s being widely reported that mobile telecoms company, T-Mobile is investigating a claim made by a hacker over the weekend of stolen data from 100 million customers. According to Bleeping Computer, the threat actor claims to be selling a data base containing birth dates, driver’s license numbers and social security numbers of 30 million people in exchange for six Bitcoin (about $270,000). This isn’t the first time T-Mobile has been targeted in a cyberattack, but the claim made by the attacker in the current instance would indicate that this time around could be different.
Not Your Typical Outcome
Without having a full scope of the details, it’s difficult to know what tactics were used in the attack, however, there are a few outcomes that can come from this type of hacker activity.
Option 1: the hacker negotiates
After gaining access and the possibility of a breach occurs, the hacker notifies the vendor (in this case T-Mobile) to work out a price to settle the issue before any damage is done. There is no indication or report that this was the case here.
Option 2: Ransomware
No surprise here as this continues to be a growing concern for organizations because criminals can demand a steep price in exchange for data to be decrypted, while there’s no guarantee that the stolen data won’t resurface down the road. Based on the reports, it doesn’t appear that T-Mobile is dealing with the typical ransomware thief.
Option 3: Data is sold on the open market.
If what the hacker claims is true, this is the current situation for T-Mobile and it’s less than ideal because it typically means that the attacker has what they claim and can prove it.
This type of extensive data harvesting is typical of a low and slow attack where attackers gain access to a system and operate undetected as they look for back doors, tap on systems, and exfiltrate data. In fact, the average global dwell time that an attacker remains inside an environment is now 24 days, according to this Dark Reading article. Time and time again, organizations that fall prey to these attacks find all the evidence to determine what happened is buried in logs and just didn't get connected in the way that it needed to for the right 'alarm bells' to go off. As we’ve pointed out during previous attacks, it’s important for organizations to recognize that hackers don’t make obvious moves, but without the visibility necessary to see and stop their motions—defending against them is nearly impossible.
According to this Bleeping Computer article, “The threat actor claims to have hacked into T-Mobile's production, staging, and development servers two weeks ago, including an Oracle database server containing customer data. As proof that they breached T-Mobile's servers, the threat actors shared a screenshot of an SSH connection to a production server running Oracle.”
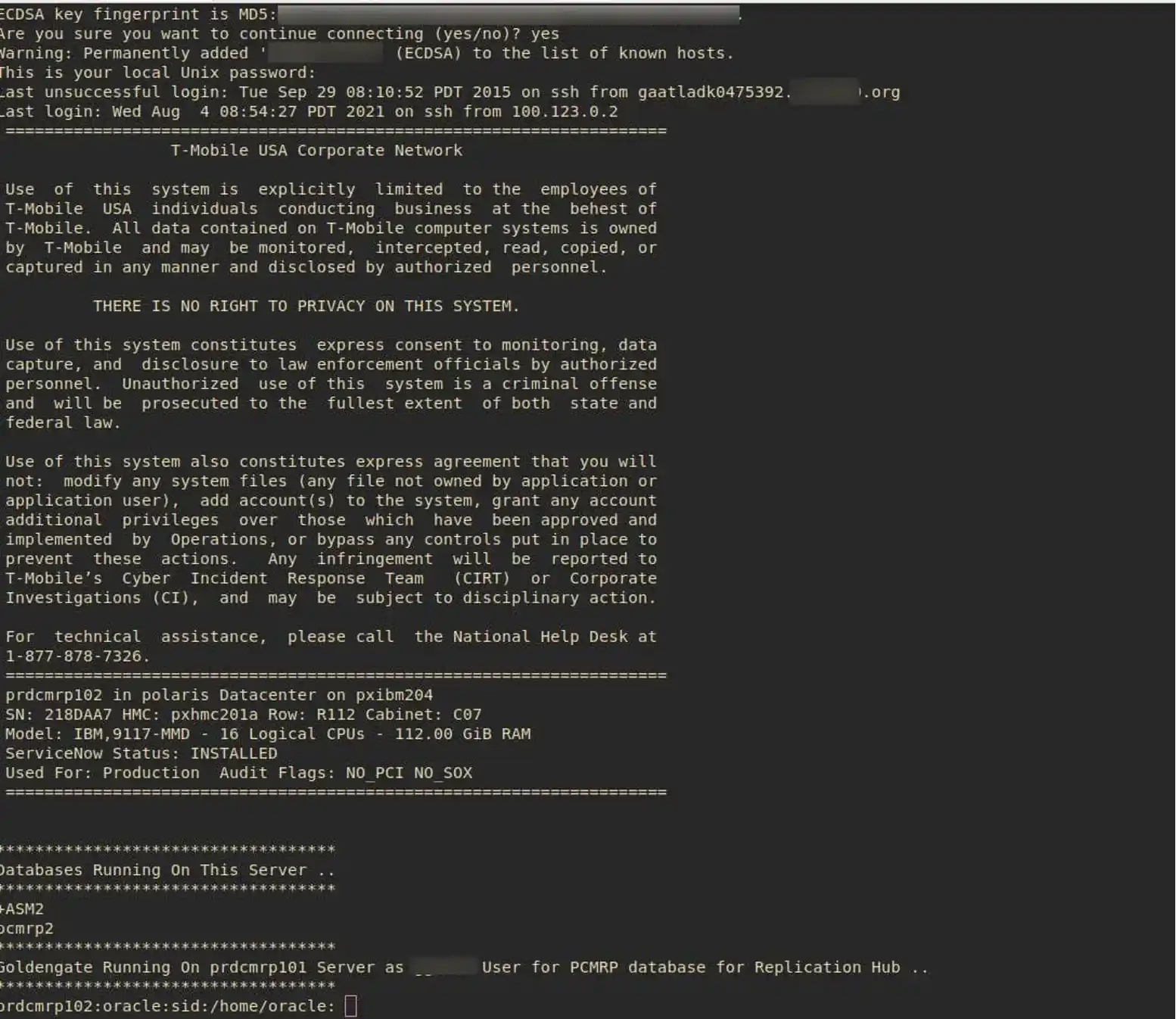
This is a developing story that our research team is actively monitoring. We will continue to post updates through our blog, including recommendations for companies concerned about persistent attacks.

