There’s a famous philosophical conundrum, around observation and perception:
“If a tree falls in a forest and no one is around to hear it, does it make a sound?”
The exact same question should be asked in detection security
"If a detection catches an attacker and no one is around to see it, is it really detected?"
At Vectra, we don’t believe it is. A detection that isn’t seen is just as good as no detection at all.
As we strive to move security forward, we believe that it is not enough to offer cutting edge security-led AI powered threat detection coverage, we also need to deliver detections in a way that a security team is able to see what is most important, so they can act on it immediately.
Fitting into Your Workflows
A key part of making sure detections can be seen, is by fitting into the way that security operations teams work.
The latest step Vectra has taken in this is a newly released version of our Splunk Integration.
Vectra's updated view is designed for the new network, where threats may be detected in your data center, from remote workers, in SaaS apps, or on the public cloud. Vectra combines all of these different data sources into a single, unified pane of glass, where the top threat to your organization (across every source) is listed, so you know exactly what to action first—be it a host or an account, on the Network, or in the cloud.
Regardless of how many attack vectors you might be worried about, Vectra will show you the number one priority based on what our algorithms say requires attention—across every surface we are monitoring.
This priority is not at a detection level, but at an entity level, which is the actual actor Vectra has spotted performing suspicious activities. This could be a host in your data center, a service account in AWS, or an Azure AD user. Vectra is able to measure the threat (how bad the attack is if it’s real), and certainty (how certain we are it’s real), to create a quadrant view, from “Low” to “Critical,” and we represent these data in the product itself.

This quadrant view is supported by a list of the top threats that require attention, so analysts know exactly what needs investigation.
“Assign” of the Times
A SOC team is only efficient when detections can be quickly alerted and communications between team members is quick and simple. To make sure no two analysts look into the same issue, Vectra makes use of its powerful “Assignments Workflow” to show who is working on which entity. Anyone who uses the “Assignments Workflow” will now be able to see who is working on entities, and if they're looking for the next item to investigate, so they can easily filter down to unassigned entities. These actions will not just save time from having to inform other colleagues about who is working on what incident, but it also powers an incredibly detailed operational metrics report.
Reporting for Duty
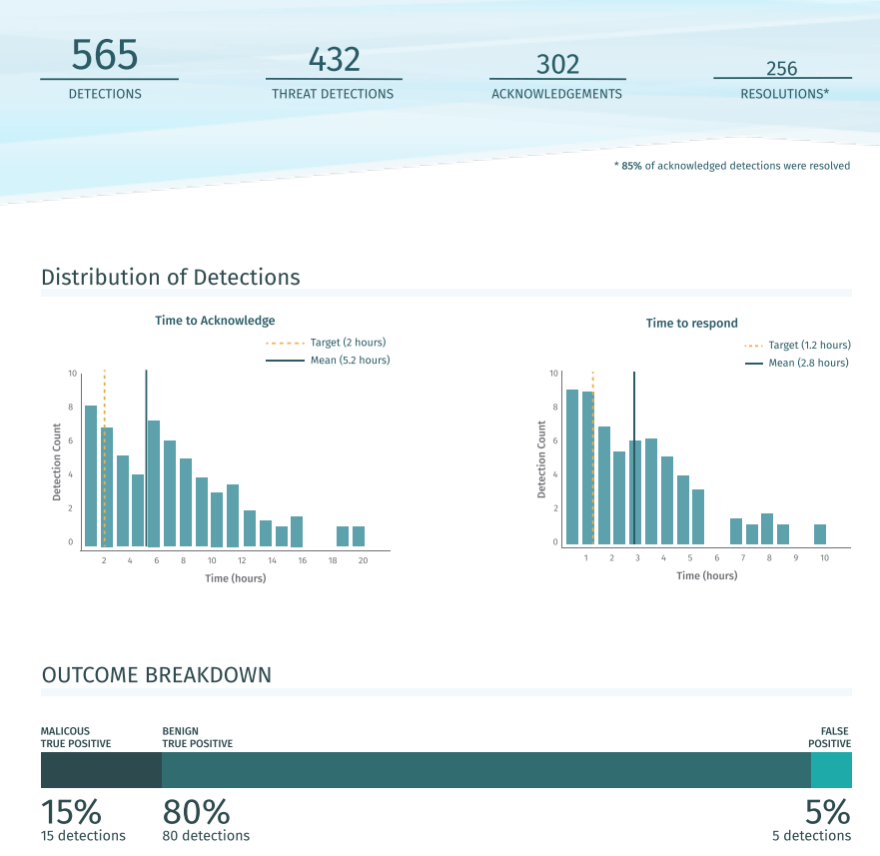
As anyone who manages systems for a living can tell you, it’s not enough to setup a working system and to leave it be—you need to monitor these systems on an ongoing basis so that you know if the efficacy of the system isn’t up to scratch. Monitoring third-party tools can oftentimes be laborious and tedious, but Vectra’s Operational Metrics Report automates this entire process by leveraging the Assignment Workflow we mentioned before, which integrates directly into your existing Splunk [JK2] workflow. With this report, managers have a clear view on how many alerts the SOC team is having to investigate, and how long it takes the team to acknowledge and respond to them on average. This is a hugely powerful tool that puts clear, hard data, behind security coverage.
When a tree falls in a Forest, catch it before it hits anything
Vectra’s Updated Splunk Integration simplifies the SOC’s workflow, and is integral to our key mission of moving security forward, so when that tree falls in the forest, your team is notified immediately, sees what’s happening and can catch it before it hits anything.
For more information about Vectra’s integration with Splunk, you can find all the details covered in the solution brief.

