Identity Threat Detection and Response (ITDR)
Identity Threat Detection and Response (ITDR)
Attackers don't hack in, they log in.
Vectra's ITDR solution finds identity attacks others can't -
protect all your accounts with less effort.

Overview
Identity threat detection, investigation, and response
Calculate your organization’s identity exposure risk
How big is your account takeover risk? It may be more than you realize. Use our calculator for a custom estimate.
3x your threat visibility with 50% less workload
With 12 references in the MITRE D3FEND framework — more than any other vendor — only Vectra AI provides identity threat detection and response (ITDR) powerful enough to give you an unfair advantage over attackers.
#1
Most-referenced in MITRE D3FEND
35
AI threat detection patents
>90%
MITRE ATT&CK coverage
Why Vectra AI
Why choose Vectra AI to defend against identity attacks?
Vectra AI's ITDR solution helps security teams with limited budgets and resources stop identity attacks early and fast.
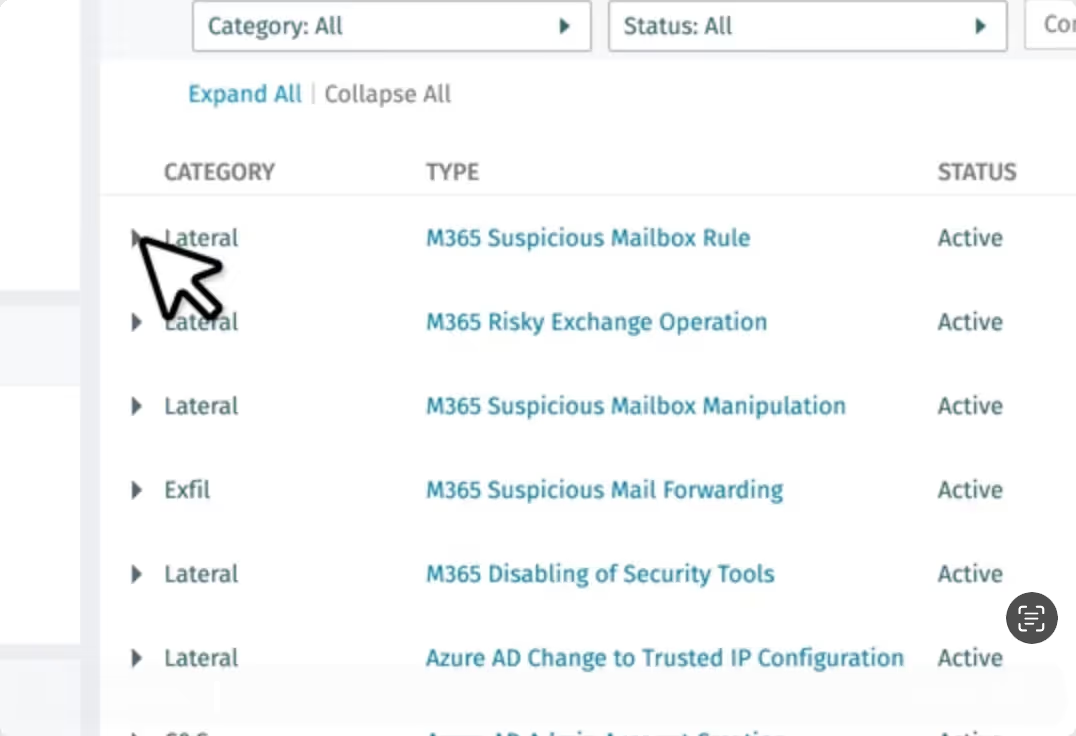
Find attackers abusing identities across your entire hybrid attack surface. Vectra AI correlates identity coverage with broader network and cloud activity to monitor for identity-based attackers using AD, Microsoft Entra ID (formerly Azure AD), local and cloud identities.
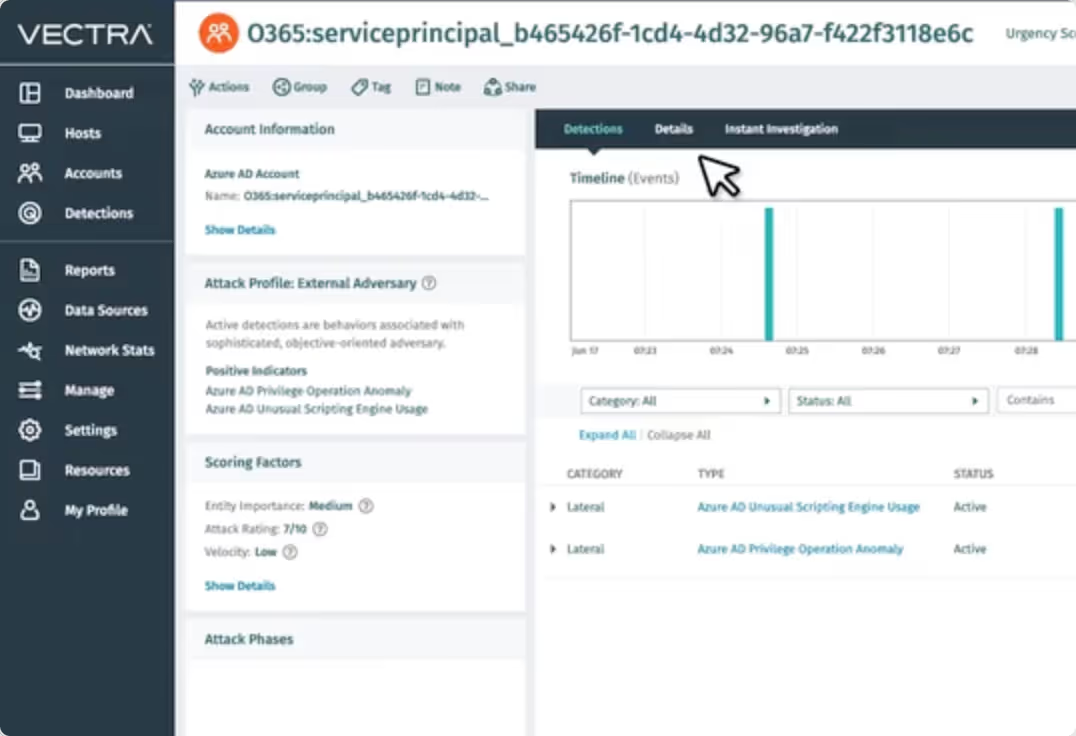
Protect service accounts — even if you don't know what they are. Our AI monitoring helps remove the risk of sprawl and keeps tabs on all service accounts to identify when they’re being abused.
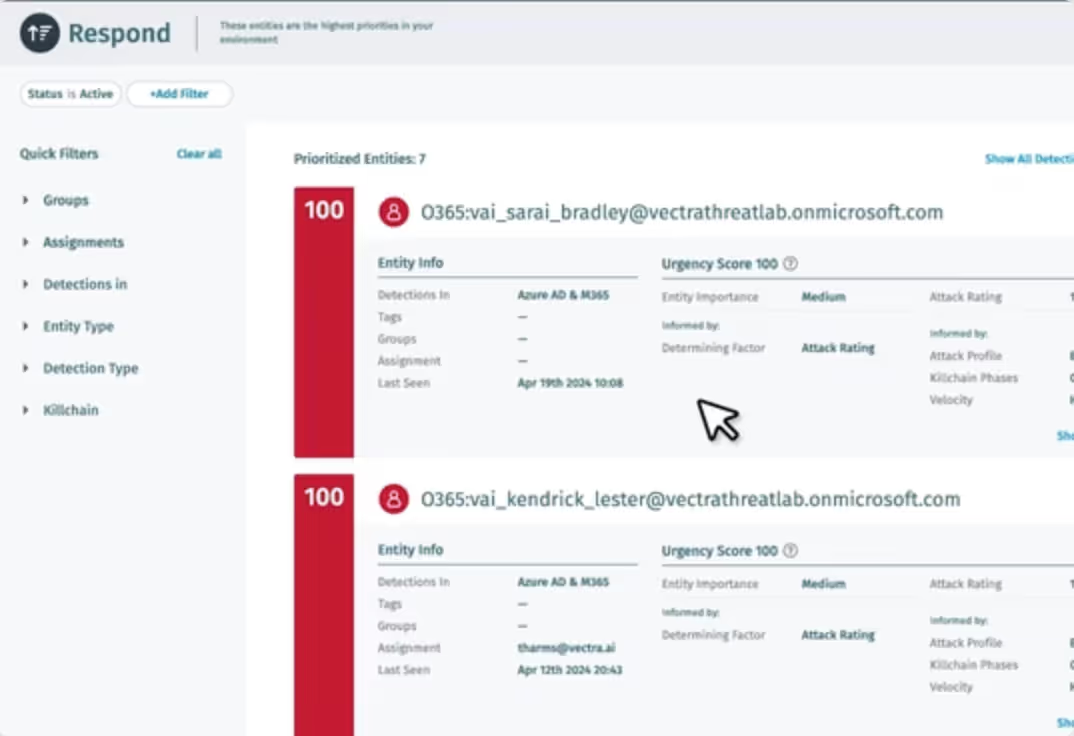
Our AI minimizes noise to provide clarity on real attacker behaviors. Simple user and entity behavior analytics (UEBA) and anomaly-based solutions fail to detect attacks — and overload analysts with alerts.

Find actors abusing identities across your entire hybrid attack surface. Vectra AI correlates threat coverage for AD, Microsoft Entra ID (formerly Azure AD), local and cloud identities with broader network and cloud threat activity to find attackers.

Protect service accounts — even if you don't know what they are. Our AI monitoring helps remove the risk of sprawl and keeps tabs on all service accounts to identify when they’re being abused.

Our AI minimizes noise to provide clarity on real attacker behaviors. Simple user and entity behavior analytics (UEBA) and anomaly-based solutions fail to detect attacks — and overload analysts with alerts.
ITDR Coverage Areas
With Vectra ITDR, detect identity attacks, anywhere in your environment
How We Help
See how Vectra AI detects identity attacks
See how Vectra AI stopped an active identity attack in minutes.

ITDR Capabilities
Finds real attacks other ITDR tools miss — long before a breach
Coverage
Detect identity-focused attackers in real time with patented AI to find the compromised identities other tools miss.
Clarity
Find attacks with fewer false positives by automatically correlating attacker actions across network and cloud to filter out benign activity.
Control
Stop attacks in minutes with simplified investigations and automated or customized response actions.
Copilot for M365 Detection and Response
Stop attackers from abusing Copilot for Microsoft 365
Secure your GenAI attack surface and stop attackers from gaining access to sensitive applications and data.
Learn more

Self-Guided Tours
Experience the power of the Vectra AI Platform
Click through at your own pace to see what analysts can achieve in a platform powered by the world's most accurate attack signal.
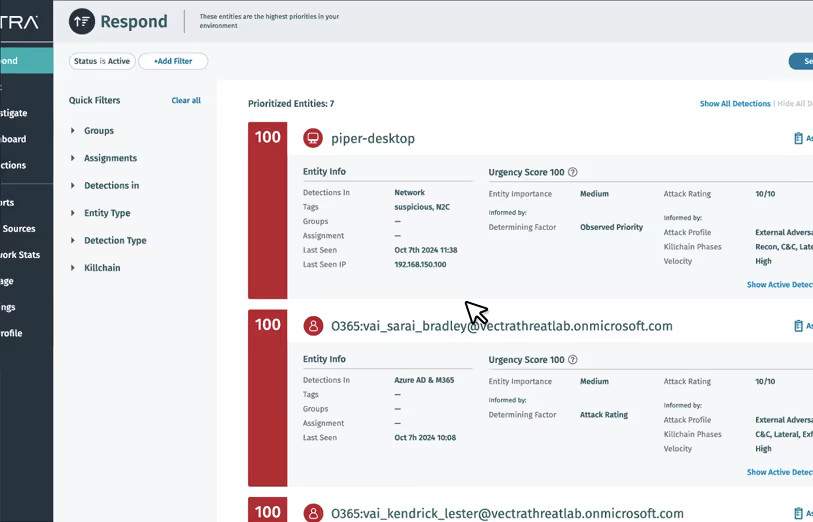

ITDR Use Cases
Most modern cyberattacks start with identities — stop them in real time

Security Team
Security architect
Security analyst
Stop ransomware by detecting attackers before they have a chance to do damage.

SOC
Security architect
Security analyst
Discover and stop attackers using spear phishing tactics to access Microsoft Entra ID (Azure AD) and connected cloud apps.

SOC
Security architect
Security analyst
Automatically monitor for all identities — human and machine.

IAM Team
Gain complete coverage for attackers targeting credentials and identity stores using techniques like kerberoasting, DCSYC and rouge LDAP queries.

Stop ransomware by detecting attackers before they have a chance to do damage.
SOC
Security architect
Security analyst

Discover and stop attackers using spear phishing tactics to access Microsoft Entra ID (Azure AD) and connected cloud apps.
SOC
Security architect
Security analyst

Automatically monitor for all identities — human and machine.
SOC
Security architect
Security analyst

Gain complete coverage for attackers targeting credentials and identity stores using techniques like kerberoasting, DCSYC and rouge LDAP queries.
IAM Team
Who We Help
Find identity threats faster and earlier with less work
Security Teams

Strengthen your defense against identity attacks to protect against data loss, ransomware and reputation damage while reducing analyst workloads by 50% or more.
Security Architects

Lighten the load for engineers to build custom models with an out-of-the-box solution that requires minimal tuning.
IAM Teams

Gain unrivaled visibility into how and where identities are being used to defend your infrastructure and support compliance.
ITDR Integrations
Native ITDR integrations for end-to-end protection
With native integrations for dozens of best-in-class security tools, Vectra's ITDR solution helps you make the most of every cybersecurity investment.















