As organizations strive to integrate cloud threat detection into operations, most face a big gap. Too often, existing tools lack flexibility to accommodate expanding use cases and extensibility to support the development of custom attack techniques.
To bridge these gaps, we’re proud to introduce the DeRF (Detection Replay Framework). Our newly released tooling addresses common challenges that arise when use cases evolve beyond isolated incidents.
The new framework incorporates several key design decisions that set it apart. It provides the separation of permissions needed for deploying the infrastructure from those needed to execute an attack. This segregation becomes increasingly valuable as capabilities expand and more users are needed to fulfill these distinct functions.
Furthermore, The DeRF was designed for extensibility. While it comes preloaded with numerous built-in attack techniques, the process of incorporating your own techniques is as straightforward as crafting a YAML file. This allows for customization without the need for modifying the core functionality of the tool.
What is The DeRF?
The DeRF, an open-source tool available on GitHub, consists of Terraform modules and a Cloud Run1 application written in Python. Within this package, a variety of built-in attack techniques are provided, focusing on AWS and GCP. The DeRF is shipped with attack technique parity with Stratus Red Team to help eliminate the need for operators to choose tooling-based attack capabilities. Instead, you can select the tooling that best suits your specific use case. For a more comprehensive look at how The DeRF compares to other cloud tools, take a look at this comparison page.
Notable built-in attack modules are listed below with a complete list of all built-in attack techniques in The DeRF documentation.
Credential Access:
Defense Evasion:
- AWS | Stop CloudTrail
Execution:
Discovery:
- AWS | EC2 Download User Data
Exfiltration:
- AWS | EC2 Share EBS Snapshot
Privilege Escalation:
Similar to other tools focused on detection generation, the DeRF deploys and manages the target cloud infrastructure, which is manipulated to simulate attacker techniques. Terraform is used to manage all resources, deploying (and destroying) hosted attack techniques and target infrastructure in under 3 minutes.
While a bring-your-own-Infrastructure (BYOI) model isn't currently supported, maintaining The DeRF infrastructure costs less than $10/month for Google Cloud and $5/month for AWS. The tool's convenient deployment model means you can use it as needed rather than continuously running 24/7. Check out the deployment guide for more details.
What sets the DeRF apart from other cloud tools?
Put simply, a lot. Key differences include:
- User-friendly interface: Since the DeRF is hosted in Google Cloud, end users can invoke attacks through the cloud console UI without the need to install software or use the CLI.
- Accessibility for non-security professionals: The DeRF caters to a broad audience of end users including engineering, sales and support staff, as well as automated processes.
- Robust OpSec: Long-lived credentials are not passed between operators. Instead, access to the DeRF and its attack techniques are controlled through GCP IAM Role-Based Access Control (RBAC).
- Extensibility at its Core: Attack sequences are written in YAML, enabling easy configuration of new techniques.
- Turnkey deployment: Deploying (and destroying!) the DeRF is a fully automated process, completed in under 3 minutes.
Getting started with The DeRF
Refer to the user guide for instructions on how to deploy The DeRF and execute your first attack technique. This guide you will walk you through:
- Deploying all resources to AWS and GCP with Terraform
- Configuring access control to the Google Cloud Workflows
- Executing an attack against either AWS or GCP by invoking a Google Cloud Workflows
How does The DeRF work?
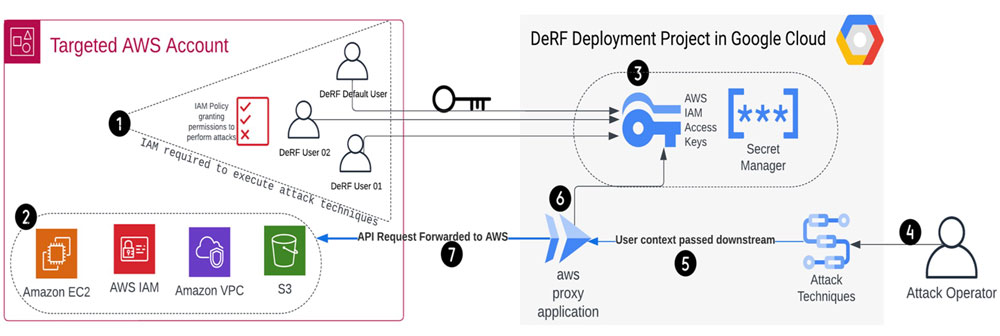
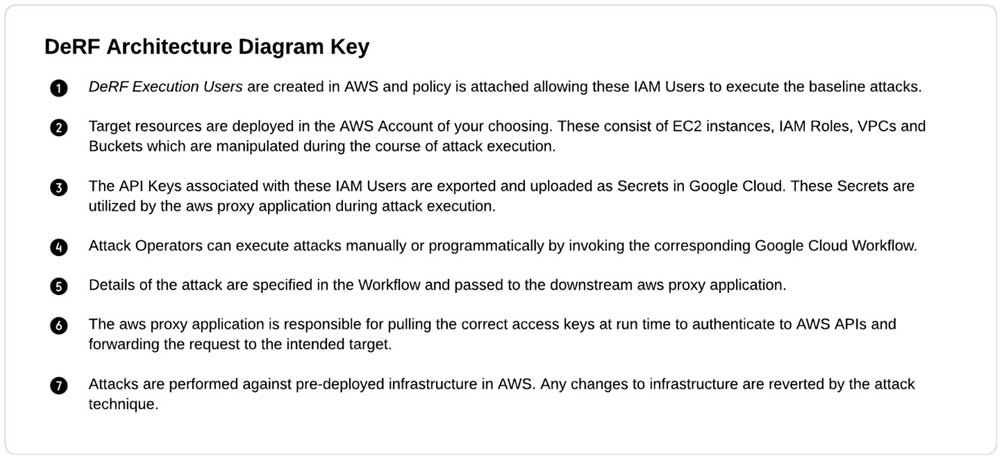
The DeRF’s unique architecture is wholly deployed via Terraform. It consists of resources spread across AWS and GCP.
The DeRF personas
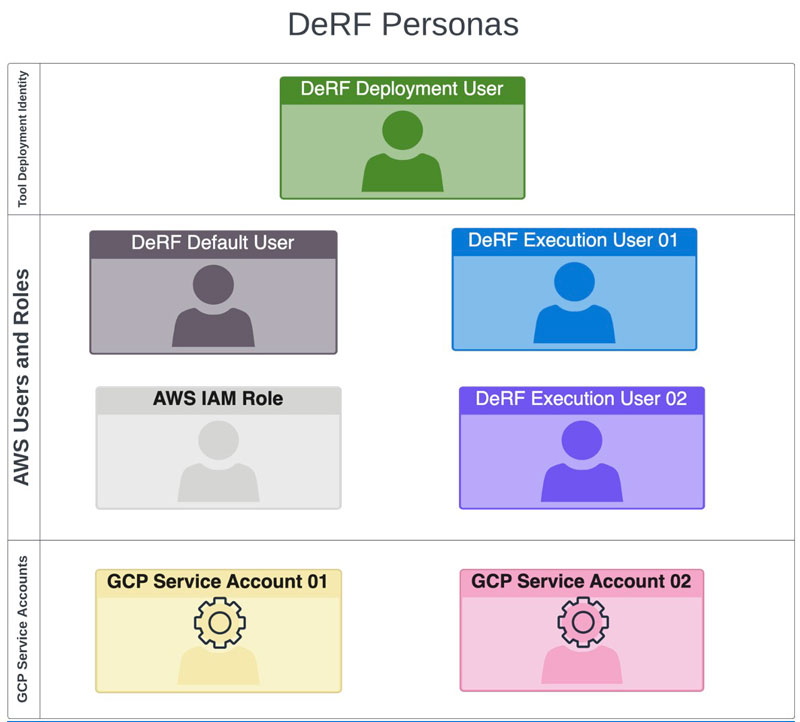
The DeRF stands out among other attack tools for its unique approach to decoupling tool deployment from attack execution. With The DeRF, operators can select different users when launching attacks. This choice serves multiple purposes, such as constructing realistic threat actor scenarios or distinguishing behaviors in the logs. For more information on available personas, including the "DeRF Deployment User,” “DeRF AWS Execution User 01,” “DeRF AWS Execution User 02," "DeRF AWS Default User," and "AWS Custom IAM Role," please consult The DeRF documentation.
Executing attack techniques
Whether your target is AWS or GCP, attacks are always executed by invoking Google Cloud workflows. Below is an example of how to execute attack techniques, whether manually or programmatically deployed with The DeRF.
Attack Execution – Manual
1. Log into the Google Cloud Console and navigate to the workflows page.
2. Click on the name of the workflow that matches the attack you want to execute.
3. Click on the execute button.
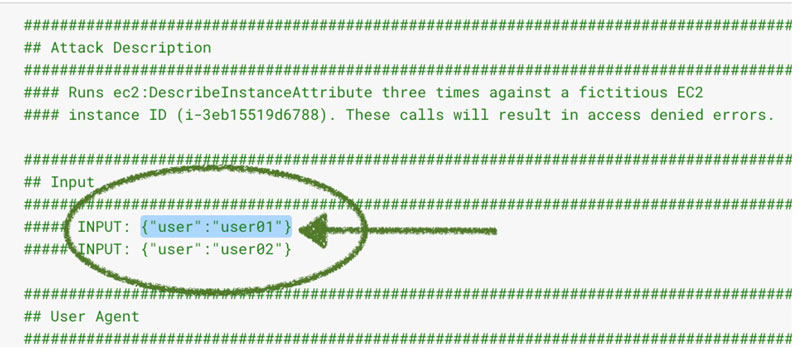
4. Refer to the Code panel on the right-hand side and select which user to run the attack as by copying one of the possible inputs.
5. Paste selected JSON in the input panel on the left-hand side.
6. Finally, select the "Execute" button at the bottom of the screen.
7. The results of the attack will be displayed on the right-hand side of the screen.
Attack Execution –Programmatic
1. Ensure the Google command line tool is installed on your local system. Reference Google maintained documentation for instructions on installing the gcloud cli.
2. Authenticate to Google Cloud Project which DeRF is deployed.
3. Invoke a particular attack techniques' workflow with the gcloud cli. See Google documentation for more comprehensive instructions on the workflows service.
Example Usage:
Creating custom attack techniques
The initial release of The DeRF encompasses a wide range of prevalent cloud attack techniques, providing your organization with ample resources for training, controls testing and executing on attack scenarios. However, as needs evolve, you may need to expand beyond the initial set and introduce your own custom attack modules. With The DeRF, this process is simplified. All attack techniques are defined as Google Cloud Workflows, which can be deployed as additional terraform modules within your forked version of the codebase.
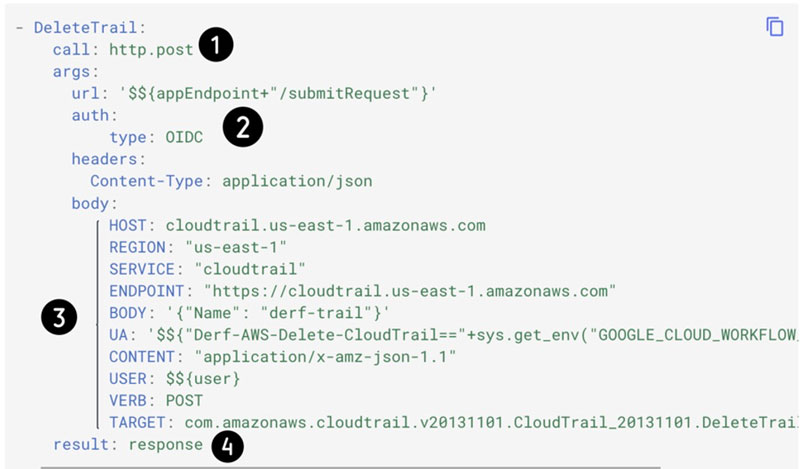
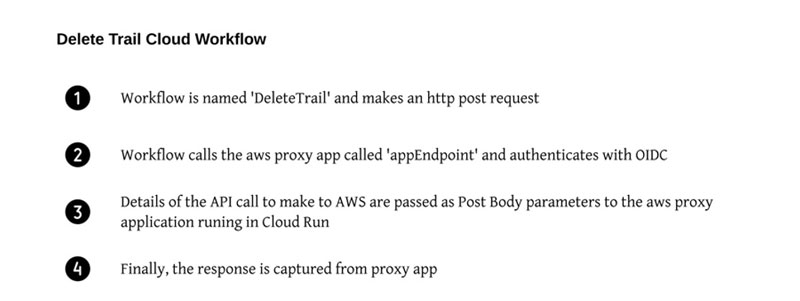
Specifying the details of an AWS API call
Every API call made to AWS is explicitly defined within an HTTP request submitted by a Google Cloud Workflow to the aws proxy application for routing to its intended destination. Comprehensive instructions on constructing an AWS attack technique as a Google Cloud Workflow can be found in The DeRF documentation. Take a closer look below to understand the construction of these workflows.
What’s next?
Next up, we plan to:
- Expand built-in attack techniques.The initial release of the DeRF is focused on attack module parity with Stratus Red Team for AWS and GCP. In the future, we’ll be releasing attack techniques unique to the DeRF through the tool and adding support for Azure.
- Add automation for invoking attack techniques. A common use case of the DeRF is continuous controls validation and detection logic testing.
Currently, Cron jobs need to be created manually to invoke attack techniques. In the near future, the DeRF will support attack technique automation through the configurations of Cloud Scheduler2.
Acknowledgements
We’d like to thank the creator and maintainer of The DeRF, Kat Traxler along with following community members for providing their support and feedback during project development:
- Christophe Tafani-Dereeper from DataDog
- Nick Jones from WithSecure
- Rich Mogull from Firemon
Engage with us directly regarding this blog post and other topics in the Vectra AI Reddit community.
References:

