While ransomware attacks like NotPetya and WannaCry were making headlines (and money) in 2017, cryptocurrency mining was quietly gaining strength as the heir apparent when it comes to opportunistic behaviors for monetary gain.
The message below posted on reddit highlights the severity of the cryptocurrency mining problem facing universities. In some cases, enterprising students will mine for cryptocurrency using high-end computers or launch an army of botnets to do the job.
Where is cryptocurrency mining most prevalent?
As the value of cryptocurrencies like bitcoin, Ethereum and Monero increased, there was a corresponding uptick in the number of computers on university campuses performing mining or cryptojacked by miners to process cryptocurrency hashes.
An analysis by Vectra of the top five industries exhibiting cryptocurrency-mining attack behaviors from August 2017 through January 2018 shows that higher education easily surpassed the remaining four combined.
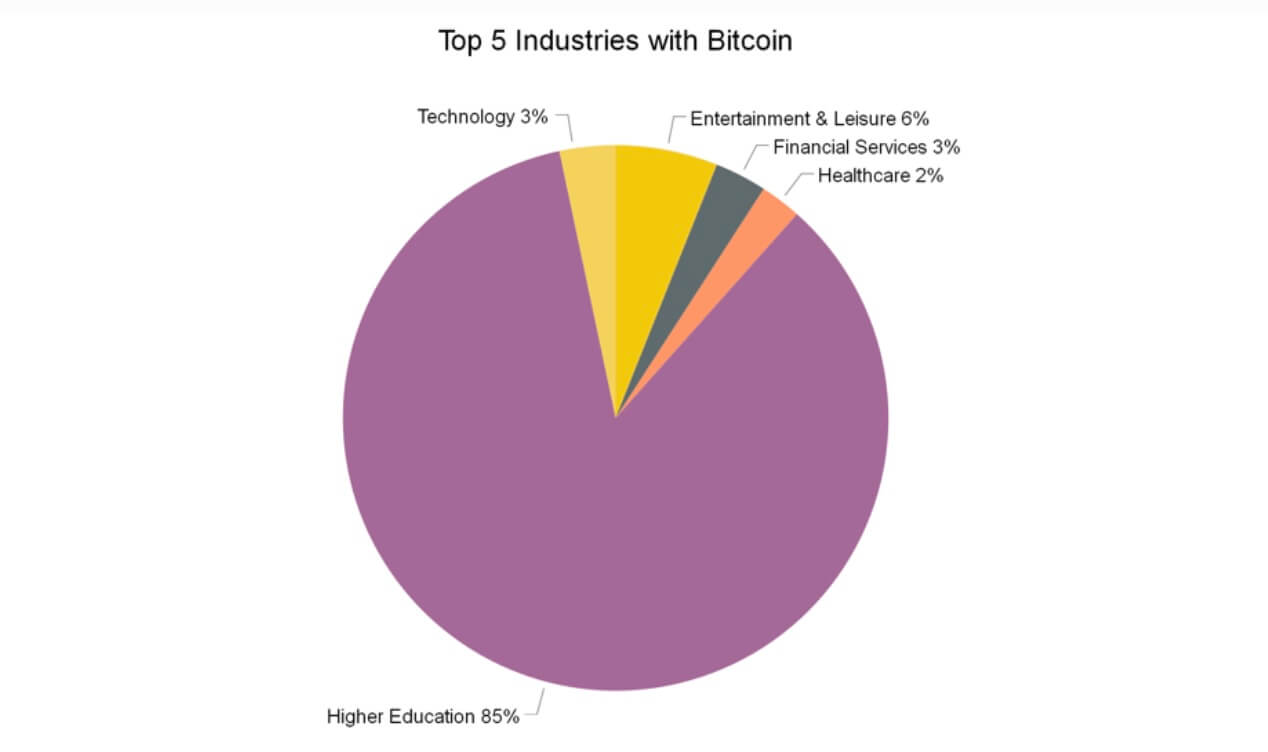
Source: 2018 RSA Edition of the Attacker Behavior Industry Report from Vectra
Why universities?
Cryptocurrency mining converts electricity to monetary value by using computational resources. This is very expensive to accomplish without a free source of power and a lot of computing resources with minimal security controls that are exposed to the internet. Large student-populations are ideal pastures for cryptojackers.
Corporate enterprises enforce strict security controls to prevent cryptocurrency mining behaviors. However, universities do not have the same luxury with students. They can at best advise students on how to protect themselves and the university by installing operating system patches and creating awareness of phishing emails, suspicious websites and web ads.
Students who mine cryptocurrency are simply being opportunistic as the value of cryptocurrencies surged over the past year, with the value of bitcoin peaking at $19,000 (source: Coinbase) in January 2018. Even at the current value of $9,000 per bitcoin, it remains a lucrative temptation.
The number of computers processing cryptocurrency hashes on college campuses increased before the value of bitcoin rose above $4,000 in 2017. The charts below show that cryptocurrency mining activity increased 30 days before the rise of bitcoin value.
Cryptocurrency mining detections increased before the price peaked
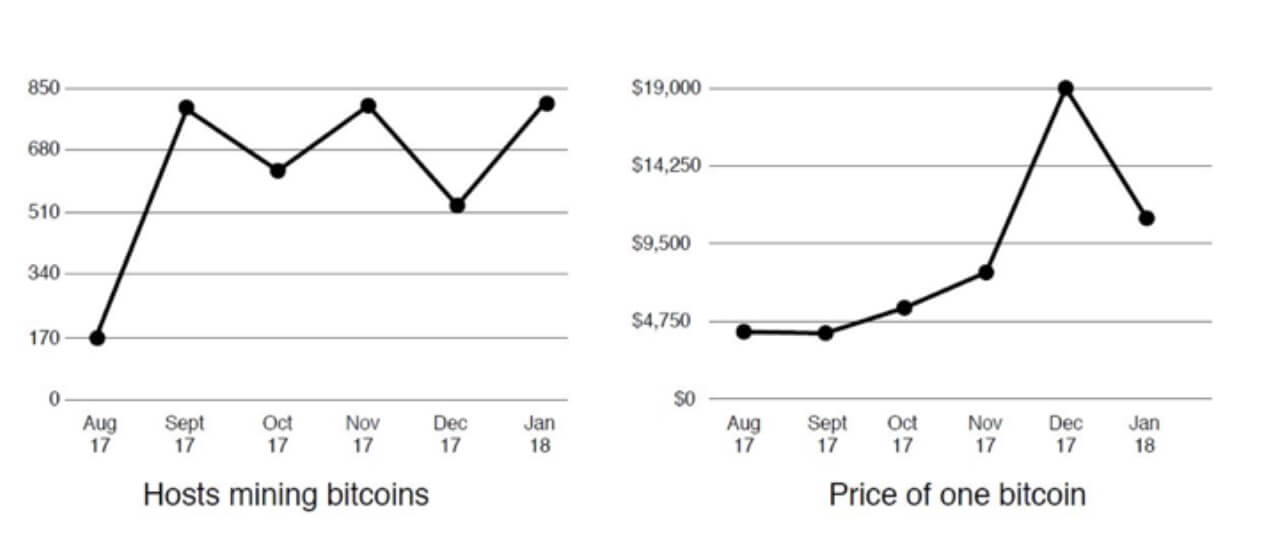
Source: 2018 RSA Edition of the Attacker Behavior Industry Report from Vectra
Even as the value of bitcoin fell 50% from its peak to below $10,000, the number of computers performing cryptocurrency mining did not decline.
Unfortunately, wherever a student or attacker exploits an opportunity, the university pays the costs of electricity and exposure to further risk. Contrary to belief of the college student’s posting on reddit, electricity is not free.
Why is it dangerous?
Cryptocurrency mining is an opportunistic attack behavior that uses botnets to create a large pool of computing power. It is considered more of a nuisance than a targeted cyberattack that puts personally identifiable information (PII), protected health information (PHI) and financial data at risk. But in some instances, these botnet activities present a high risk to organizations:
- They create noise that can may hide serious security issues;
- They impact the reputation of an organization’s IP address, causing it to be black listed;
- Cybercriminals will buy access to compromised computers from cryptojackers to launch targeted attacks against universities.
If computer users intentionally install cryptocurrency mining software, the risk may be minimal, although they could also install other money-making software that presents a greater risk.
Cryptocurrency mining eats up a system’s computing power. As a result, infected systems sustain increased wear and tear from processing cryptocurrency blocks, making infected systems work abnormally slow.
Although cryptomining malware does not target individuals, cybercriminals can infect systems that use high-performance graphic processing units (GPUs) or video cards. This speeds-up the GPU-intensive hashes used by cryptocurrencies like bitcoin. Gamers and other users of graphics-intensive applications are especially juicy targets.
Cryptojacking is king
The lack of computers driven by high-end GPUs gave rise to a new type of in-browser cryptocurrency mining that leverages ordinary CPU power. Dubbed cryptojacking, it does not require a program to be installed and can occur simply by visiting a website.

When Coinhive launched in September 2017 and kicked-off the cryptojacking frenzy, the internet went crazy with in-browser cryptocurrency miners. New sites that offer similar services continue to pop-up on a weekly basis, enabling miners to produce the Monero cryptocurrency.d
While mining Monero in a website’s background might be a viable alternative to viewing intrusive ads, almost none of these services lets users know what’s happening or stops the mining behavior. Most behave like malware, secretly commandeering computers and using resources without permission.
What is the impact?
Cryptocurrency mining is measured by the number of attempts to find a block a miner can perform. Each attempt involves creating a unique block candidate and creating a digest of the block candidate using SHA-256d, a cryptographic hash measures in hashes per second (h/s).
Since September 2017, in-browser mining for Monero has skyrocketed. Monero mining requires calculating hashes using an algorithm called CryptoNight. This algorithm is compute-intensive and, although slow, runs well on consumer CPUs.
It is possible to run the CryptoNight algorithm on a GPU, but the benefit is about 2x, not 10,000x, as it is for other algorithms used by bitcoin or Ethereum. This makes CryptoNight a target for JavaScript and the browser because it is easy to build a script that scales to a large set of systems for distributed pool mining.
When run through JavaScript, mining performance is impacted but still acceptable. The miner uses WebAssembly and runs with about 65% of the performance of a native miner. An Intel i7 CPU, one of the fastest desktop CPUs, produces about 90 h/s. A native miner gets 140 h/s. CPU-based mining is sufficient for botnets.
Using a Monero performance calculator, a rate of 90 h/s across 812 devices that are mining 24/7 produces these results:

Key takeaways
Cryptojacking and cryptocurrency mining are profitable, opportunistic endeavors that will likely increase as they replace ransomware and adware as the de facto method for individuals looking to make a fast buck.
To learn more about other types of cyberattack behaviors seen in real cloud, data center and enterprise environments, get the 2018 RSA Conference Edition of the Attacker Behavior Industry Report from Vectra.

