SMS-based two-factor authentication (2FA) was once considered a reliable safeguard, but attackers have long since found ways to exploit its weaknesses. From account takeovers caused by recycled phone numbers to SIM swapping campaigns by groups like Scattered Spider, SMS-based MFA exposes organizations to avoidable breaches. What may start as a personal inconvenience—such as losing access to a Google or Amazon account—can quickly escalate into corporate compromise, financial fraud, and data exfiltration.
This blog highlights real-world examples and advanced attacker playbooks to show why SMS 2FA is no longer defensible as a security control, and what executives must do to protect their organizations.
Real World Example: Why is SMS 2FA Not Secure
A couple of years ago, I had to set up a new phone number and I quickly learned just how fragile SMS-based multi-factor authentication (2FA) can be. My first surprise came with my Amazon account. The number I had just acquired was still tied to another person’s account.
When I tried to secure my own account, I discovered how easy it would have been for someone else to access it. Amazon allows users to log in with a mobile number and bypass the password altogether by requesting a one-time passcode (OTP) sent via SMS. In practice, this means that anyone holding a phone number linked to an account can receive the code and gain entry without ever knowing the original password.

Once inside, the individual can reset the account password, change the associated email, and even make purchases using stored credit card details. Critically, Amazon does not require additional bank validation for these transactions, so a determined attacker could exploit this flaw for fraudulent activity.

In my case, I unintentionally accessed the previous owner’s account but immediately stepped back and disassociated the number so I could secure my own. This incident illustrates how SMS-based authentication opens the door to account takeover risks. For a business, the consequences go far beyond personal inconvenience. If this scenario played out with a corporate account, the result could be unauthorized financial transactions, data loss, and a direct hit to customer trust.

This simple example shows why SMS-based 2FA, while convenient, is not secure. A phone number can be reassigned, intercepted, or hijacked, and with it, an attacker gains the keys to the account. For executives evaluating enterprise risk, this is not just a user-level problem, it is a systemic vulnerability that advanced attackers actively exploit.
Multi-Factor Authentication Vulnerabilities
When I changed my phone number but forgot to update it on my Google account, I was locked out despite knowing my password. The login process required a verification code sent to my old number, and since that number no longer belonged to me, I couldn’t receive it. For an executive or employee, this scenario can mean losing access not only to email, but also to Google Drive files, shared documents, and third-party applications tied to Google authentication.

This personal inconvenience highlights a larger issue: SMS-based MFA creates single points of failure that attackers can exploit. Unlike app-based or phishing-resistant authentication, SMS one-time passcodes (OTPs) can be intercepted, redirected, or hijacked.
Over the past few years, several attack techniques have emerged that make this risk a reality for enterprises. Here are the top 3:
- SIM swapping (or SMS swapping): Attackers convince mobile carriers to transfer a target’s phone number to a SIM card they control. Once successful, they receive all SMS messages intended for the victim, including MFA codes. This technique has fueled financial fraud and corporate breaches costing organizations millions.
- Social engineering: Attackers can trick employees into resetting MFA settings, and exploiting SMS-based verification. Groups like Scattered Spider have successfully bypassed SMS 2FA in multiple high-profile breaches, proving how effective targeted social engineering can be when combined with SMS vulnerabilities.
- Mass number exploitation: Attackers purchase blocks of recycled or unused numbers, betting that some remain linked to online accounts. With bulk automation, they test for accounts tied to those numbers and attempt takeovers.
Each of these attack vectors shows why SMS-based MFA is not a reliable safeguard against modern threats. For organizations, the impact is much more serious than a locked-out account. These vulnerabilities create entry points for account takeover, lateral movement inside networks, and data exfiltration, all of which advanced groups like Scattered Spider actively weaponize.
Executives must see SMS-based MFA for what it is: a convenience measure, not a security control. In high-risk environments, it exposes the business to preventable breaches. Transitioning to phishing-resistant MFA methods such as security keys or passkeys, combined with continuous monitoring for abnormal identity behavior, is essential for reducing this risk.
After SMS 2FA Is Bypassed: How Attackers Move, a Scattered Spider Example
When attackers bypass SMS-based MFA, the compromise rarely stops at a single account. For executives, the real danger is what follows: credential misuse, stealthy persistence, and rapid escalation into critical systems. Below is a concise, executive-friendly breakdown of the typical attack progression, illustrated with tactics used by Scattered Spider, a group known for combining social engineering and SIM swapping to defeat SMS 2FA.
Typical attacker progression after SMS MFA bypass
- Immediate account control: With an SMS one-time code in hand, the attacker logs in as the legitimate user. They can perform actions that look normal, which helps them avoid basic alerts.
- Secure foothold, reduce friction: The attacker changes recovery options, adds alternate emails or phone numbers, and resets the password to prevent the real user from reclaiming access.
- Escalate privileges in SaaS: Next they target identity and collaboration platforms, such as Office 365 or Google Workspace, seeking admin-level settings or mailbox permissions. Small changes such as delegation, inbox rules, or forwarding can give long-term visibility into communications.
- Create persistence and backdoors: Attackers add service principals, forged trust relationships, or API tokens. These elements look legitimate on paper, and they let the attacker return even if a stolen credential is rotated.
- Pivot to cloud and critical assets: With valid identity tokens and delegated rights, attackers probe cloud workloads, storage, and administrative panels, looking for sensitive data, credentials in code repositories, or misconfigured services.
- Exfiltrate, monetize, or sabotage: Finally they export data, move funds, or deploy ransomware. Because the activity originates from legitimate accounts, detection and response can be slower, increasing business impact.
Scattered Spider, as an illustrative playbook
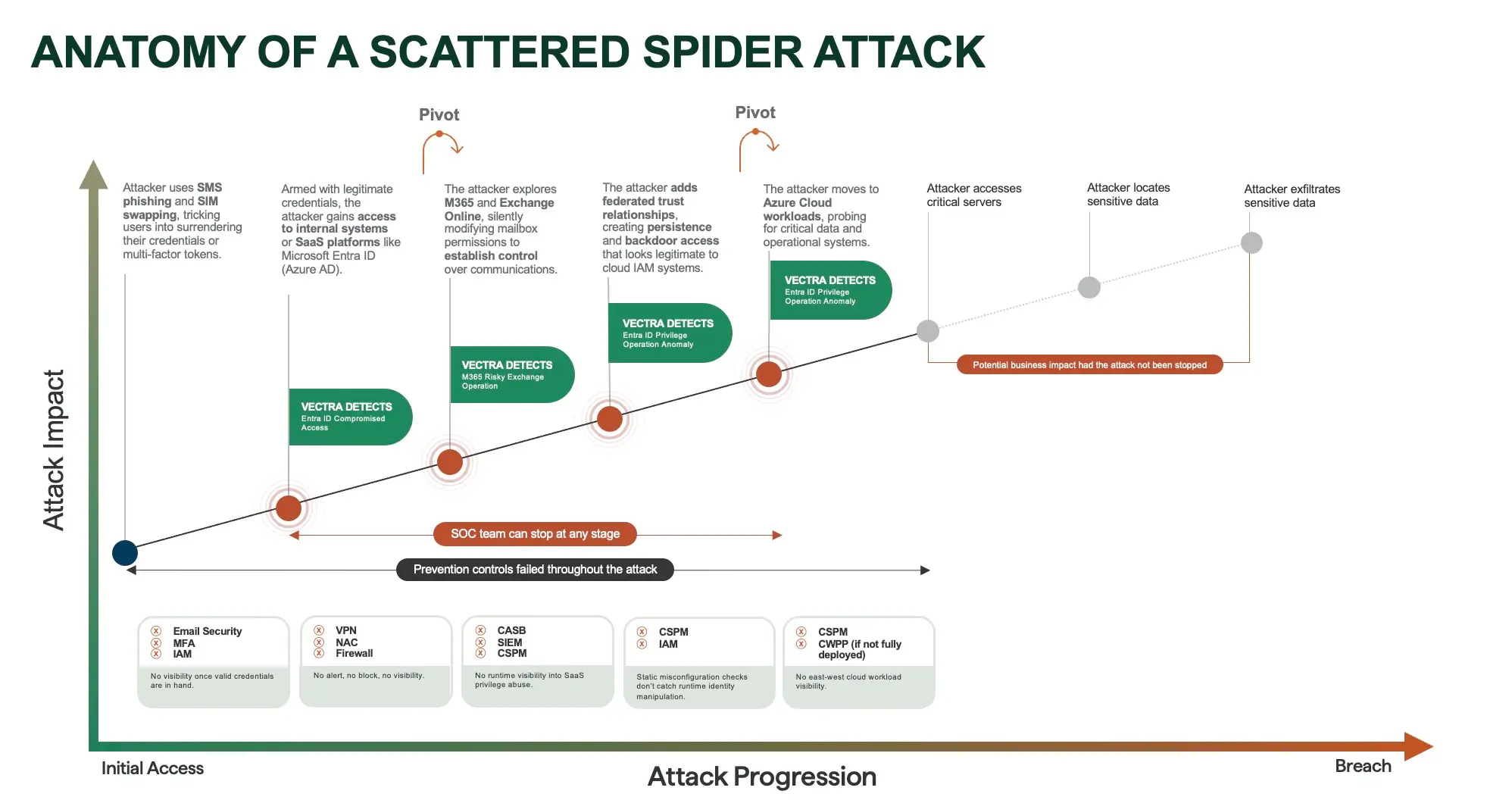
Scattered Spider uses social engineering as the opening move, often targeting help desk staff or customer support to enable SIM swaps or MFA resets. Their approach typically follows these steps:
- Targeted social engineering, convincing carriers or support teams to transfer phone numbers or approve MFA changes.
- Use of SIM swaps or redirected SMS, receiving OTPs and authenticating as the victim.
- Rapid privilege harvesting, accessing SaaS admin consoles and enabling mailbox forwarding or API access.
- Establishing legitimate-looking persistence, such as federated trust relationships or service principals that blend into normal cloud configurations.
- Lateral movement into high-value systems, where exfiltration or financial fraud can occur.
Why Enterprises Must Retire Text Message MFA: Strategic Risks and Safer Alternatives
The weaknesses of SMS-based multi-factor authentication go far beyond personal accounts. For enterprises, they represent a systemic security gap that can be exploited to devastating effect. A single phone number hijack or intercepted one-time passcode is enough for an attacker to pose as a trusted user and slip past perimeter defenses.
Groups like Scattered Spider have shown just how far these weaknesses can be weaponized. By using SIM swapping and social engineering, they have successfully bypassed SMS-based MFA, gained access to identity systems like Entra ID, and established long-term persistence in cloud environments. In some cases, these tactics have contributed to breaches costing companies tens or even hundreds of millions of dollars in direct losses and recovery efforts.
For executives, the implications are clear:
- Financial and operational impact: Compromised accounts can lead to fraudulent transactions, downtime, and regulatory penalties.
- Reputational damage: Customers and partners lose confidence when attackers exploit such avoidable vulnerabilities.
- Strategic liability: Clinging to SMS-based MFA leaves the organization exposed to methods attackers actively industrialize.
The path forward requires phishing-resistant MFA methods such as FIDO2 security keys, passkeys, or biometrics. Unlike SMS codes, these cannot be redirected or intercepted, making them resilient against SIM swap and phishing campaigns. Agencies such as CISA already recommend these standards as best practice for enterprises handling sensitive data.
Technology, however, is only one side of the equation. A security-first culture must reinforce these measures. Employees need awareness training to recognize social engineering ploys, such as fraudulent IT support calls designed to reset MFA. Combined with continuous identity threat detection and AI-driven monitoring, organizations can shut down abnormal activity before it leads to a breach.
The bottom line for leadership is simple: SMS-based MFA is no longer defensible as a corporate security control. Replacing it with phishing-resistant alternatives and pairing that with continuous detection ensures stronger protection, resilience against advanced groups like Scattered Spider, and long-term preservation of business trust.
--
To better understand how attackers are bypassing weak MFA implementations and why this blind spot remains a pressing risk for enterprises, explore our blog post: Attackers Don’t Hack In – They Log In: The MFA Blind Spot.

