Credential Access
Brute-Force
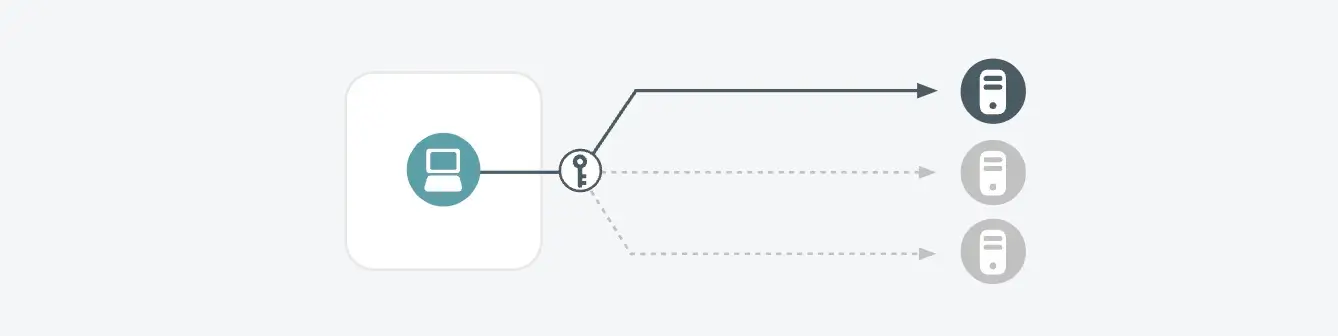
Detection overview
The "Brute-Force" detection focuses on identifying attempts to gain unauthorized access to user accounts through repetitive guessing of passwords. Brute-force attacks involve trying numerous combinations of usernames and passwords until the correct one is found. This detection is crucial as successful brute-force attacks can lead to unauthorized access, data breaches, and further exploitation within the network.
Triggers
- An internal host is making many login attempts on an internal system, behavior which is consistent with a brute-force password attack
- Such attacks can be performed via different protocols (e.g. RDP, VNC, SSH) and may also be a Heartbleed attack (e.g. memory scraping)
Possible Root Causes
- An infected host or a malicious insider in control of the host is trying to guess passwords on another internal system
- A misconfigured host is constantly trying to connect to one or more other internal systems
Business Impact
- Successful harvesting of account credentials (usernames and password) of other accounts, particularly more privileged accounts, is a classic progression of a targeted attack
- Even if triggered due to a misconfiguration, the identified misconfiguration is creating significant stress on the target system and should be cleaned up
Steps to Verify
- Determine whether the internal host in question should be connecting to the target host; if not, this is likely malicious behavior
- Determine which process on the internal host is sending traffic to the internal IP address(es) and ports; in Windows systems, this can be done using a combination of netstat and tasklist commands
- Verify that the process should be running on the infected host and whether the process is configured correctly
Brute-Force
Possible root causes
Malicious Detection
- An attacker is attempting to brute-force user accounts to gain unauthorized access.
- Use of automated tools or scripts to perform brute-force attacks on login portals.
- Insider threat where an employee is attempting to access restricted accounts.
Benign Detection
- Users forgetting their passwords and repeatedly attempting to log in.
- Misconfigured applications or systems causing repeated login attempts.
- Penetration testing or security assessments involving brute-force attack simulations.
Brute-Force
Example scenarios
Scenario 1: An attacker uses a tool to perform a brute-force attack on a company's VPN login portal. The tool tries various combinations of usernames and passwords until it successfully gains access to an account. This detection is triggered by the high number of failed login attempts from a single IP address.
Scenario 2: During a penetration test, the security team simulates a brute-force attack on several user accounts to test the organization's defenses. The detection is triggered, and the activity is verified as part of the scheduled assessment.
Brute-Force
Business impact
If this detection indicates a genuine threat, the organization faces significant risks:
Account Compromise
Unauthorized access to user accounts can lead to further exploitation and data breaches.
Privilege Escalation
Compromised accounts with elevated privileges can be used to gain further access within the network.
Operational Disruption
Repeated login attempts can overwhelm authentication systems, causing delays or outages.
Brute-Force
Steps to investigate
Review Login Attempt Logs
- Check authentication logs for patterns of failed login attempts, including timestamps, source IP addresses, and usernames.
- Identify any unusual login patterns or spikes in authentication failures.
Correlate with User Activity
- Verify if the affected accounts are associated with legitimate users who may have forgotten their passwords.
- Check for any recent changes in user behavior or account privileges.
Examine Tools and Scripts
- Check for the presence of any known tools or scripts used for brute-force attacks.
- Review any automated tasks or scripts that may be causing repeated login attempts.
Conduct a Threat Hunt
- Search for other indicators of compromise or malicious activity associated with the same IP addresses or user accounts.
- Verify if the detected activity is part of a scheduled security assessment or penetration test.
Brute-Force
Related detections
FAQs
What is a brute-force attack?
A brute-force attack involves repeatedly trying various combinations of usernames and passwords until the correct one is found to gain unauthorized access to user accounts.
Can a brute force attack be detected?
Yes. Monitoring authentication logs for patterns of multiple failed login attempts, unusual login behaviors, and spikes in authentication failures can help detect brute-force attacks.
What are the common signs of a brute-force attack?
Common signs include numerous failed login attempts from a single IP address or user account, repeated login attempts with different usernames or passwords, and sudden spikes in authentication failures.
Why is a brute-force attack a significant threat?
Successful brute-force attacks can lead to unauthorized access, account compromise, data breaches, and privilege escalation within the network.
Can legitimate activities trigger the detection of brute-force attacks?
Yes, users forgetting their passwords, misconfigured applications, or scheduled security assessments can trigger this detection. It’s important to verify the context of the activity.
What steps should I take if I detect a brute-force attack?
Investigate the source of the login attempts, verify if they are legitimate, check for other signs of malicious activity, and take steps to secure affected accounts, such as resetting passwords and enabling MFA.
How does Vectra AI detect brute-force attacks?
Vectra AI uses advanced AI algorithms to analyze authentication logs and identify patterns indicative of brute-force attacks, correlating these with other suspicious behaviors.
What is the business impact of a brute-force attack?
The primary risks are account compromise, privilege escalation, data breaches, operational disruptions, and compliance violations, which can lead to significant damage to the organization.
How can I prevent brute-force attacks?
Implement strong password policies, use multi-factor authentication (MFA), monitor authentication logs, set up account lockout mechanisms, and regularly audit user activity and access controls.
What tools can help verify the presence of brute-force attacks?
Tools like authentication log analyzers, Threat Detection and Response systems, and specialized monitoring solutions can help identify and verify brute-force attacks.