Now that the dust from the MOVEit Transfer zero-day has settled a bit, it may be a good time for us all to take a step back and evaluate our current approach to managing the risk associated with the particularly pesky threat of zero-days. Because, if the current trend is any indication, they’re not letting up anytime soon.
Analyzing Zero-Day Trends with Microsoft's Patch Tuesday Data
To find a point of reference for a zero-day trend line, we dug into Microsoft’s Patch Tuesday data because it’s one of the few reliable sources that tracks and reports on them. And lucky for us, they make the raw data publicly accessible via the MSRC Security Updates Guide. So, we downloaded the data for the past four and a half years to mine it for some insights.
Note: Security updates that are specifically associated with vulnerabilities can be found on the “Vulnerabilities” tab or by going directly to the Vulnerabilities link. Unfortunately, this tab’s filtering capabilities are limited so, we had to download the data to Excel to get to the goodies. Thankfully, they provide a simple download button that will export the data for you.
Understanding Microsoft's Zero-Day Classification
So, what does Microsoft report as a “zero-day” anyway? They don’t explicitly call out zero-days in the MSRC Security Updates Guide. But what they do provide is a classification of whether the vulnerability was seen being exploited in the wild prior to the security update being released. And they also track whether the vulnerability was publicly disclosed, which is a handy measure of how well informed the industry was with respect to the specific vulnerability. An exploitable vulnerability with no available patch meets our standard for qualifying as a zero-day for the purpose of this report.
Examining Zero-Day Vulnerability Trends and Disclosures
By building a simple chart of how many vulnerabilities were flagged as exploited, and how many of those vulnerabilities were publicly disclosed over the past four and a half years, we can see a somewhat jarring increase in the number of zero-days in 2021. The number of public disclosures increases as well but not in proportion to the number of exploited vulnerabilities, which is somewhat concerning:
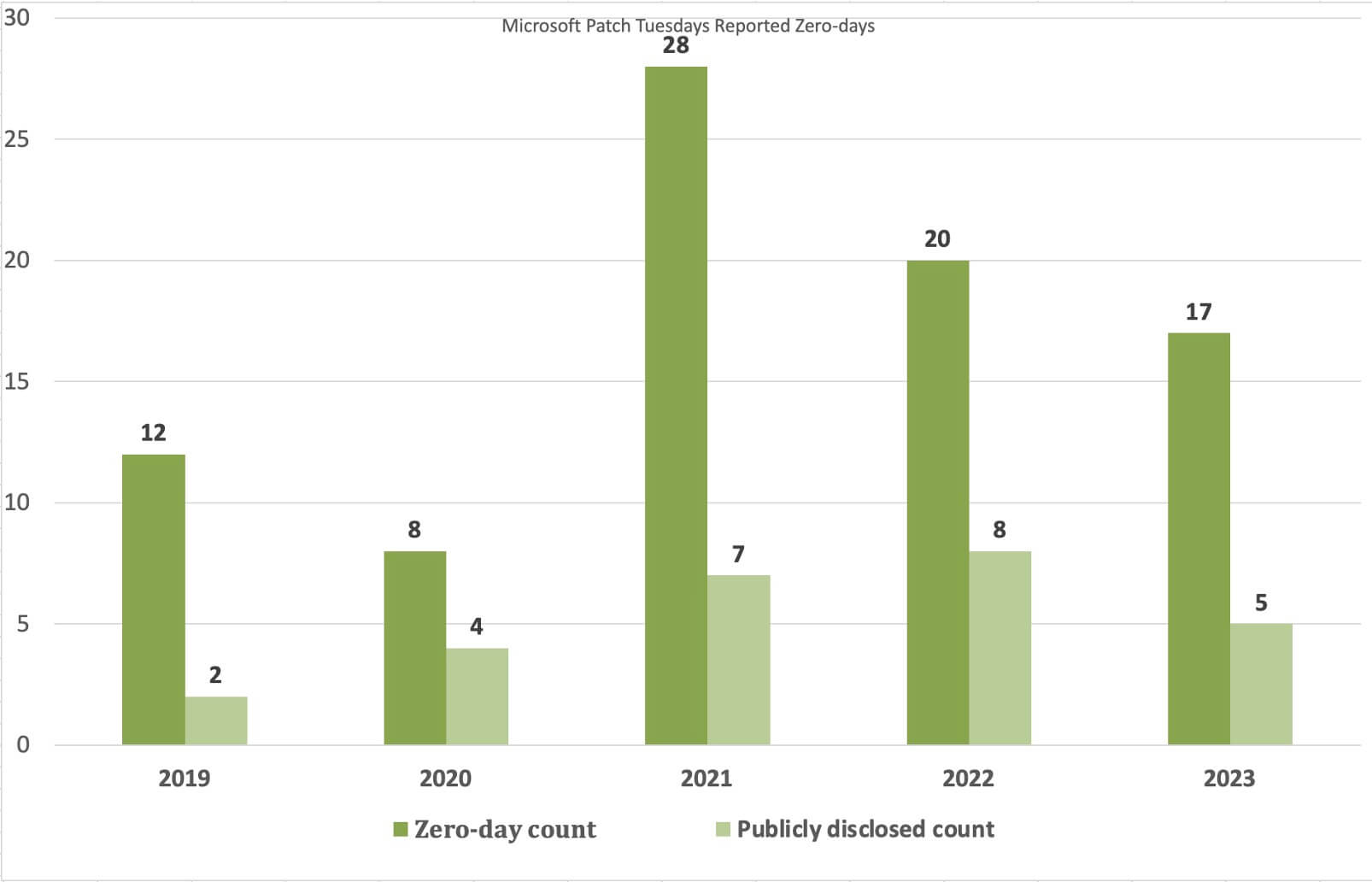
At first glance, it appears that we’re getting some relief as the trend looks to be falling off from the 2021 high but at the current rate of 17 exploited vulnerabilities at slightly more than halfway through 2023, it’s reasonable to expect that we’re on track to get back to the 2021 high.
While the number of zero-days may seem small in comparison to the total number of yearly reported vulnerabilities, it’s the percentage increase starting in 2021, compared to previous years that is remarkably concerning. In addition, more than half of the vulnerabilities were not publicly disclosed, meaning that for those vulnerabilities, defenders don’t have the opportunity to implement mitigations while waiting for a patch.
The amount of damage a threat actor can inflict with just one zero-day can be substantial when the right circumstances are in place. Each additional zero-day increases the odds of landing on a threat actor’s dream trifecta – a vulnerability that is accessible, impactful, and most importantly pervasive amongst their target demographic.
Validating Zero-Day Trends with Google's Project Zero Data
Comparing Data Sources
Obviously, the zero-day figures used above are for just one vendor so we decided it would be a good idea to look at some other data points just to make sure that the zero-day reports from Microsoft are appropriately representative of the bigger picture and it turns out, they are. The chart below is taken from data provided by Google’s Project Zero and their “0-days In-the-Wild” tracking data.

Parallel Trends in Google's Data
As in the pure Microsoft data, the Google "0-days In-the-Wild” data shows a dramatic jump in 2021, a slight retrace in 2022, and an uptick in 2023 that looks to be on pace with the figure in 2021. It would be logical to conclude that the trend is aligned due to Google’s 0day data being heavily influenced by the number of Microsoft vulnerabilities but, that’s not entirely the case. For example, in 2023, Microsoft’s data shows 17 “zero-days” while Microsoft vulnerabilities only account for 10 “0days” in Google’s data. In 2022, the number was 11 compared to Microsoft’s 20 reported zero-days. Regardless of the recording discrepancies in the two different sources, the trend seems to hold.
Correlating Ransomware Attacks with Zero-Day Vulnerabilities
As we looked at the data, we developed a hunch that another trend might align with this one. So, we turned to BlackFog’s State of Ransomware reports for some statistics about the number of publicly reported ransomware attacks:

Note: Blackfog does not have data for 2019 so we assigned the same value to that year as 2020 to not significantly skew the appearance of the chart. Links to the Blackfog reports are included at the end of this brief.
As noted in the first chart, with 250 public ransomware reports through seven months of 2023, it’s reasonable to expect the trend will hit at least the previous high of 376 reports.
While not reflected in the above chart, it is also worth noting that the month-by-month reports of ransomware incidents reported in 2020 were relatively stable until September, when the number of reports jumped by 66% over the previous month and remained elevated through the remainder of the year. (View Blackfog’s report for 2020 to see a month by month representation of ransomware attacks.)
We found it interesting that the spike at the end of 2020 preceded such a dramatic jump in the number of zero-day reports in 2021.
Leveraging AI to Defend Against Zero-Day Exploits
At best, the figures above are just an interesting correlation, but it does illustrate one important point: The trends show a steady increase of both zero-day reports and public disclosures of ransomware attacks. When taken together, they represent a logical but concerning situation for Cybersecurity defenders, which is that it’s reasonable to assume that a highly motivated group of attackers continue to possess a bevy of sophisticated weaponry with which to carry out their misdeeds.
If these trends persist, defending against attacks that are nearly impossible to prevent is going to be a mainstay in the normal routine of a cybersecurity organization. As such, a reliable method for detecting attackers that are employing zero-day exploits will be a necessity for teams that expect to be successful in this endeavor. And this is where AI can be a game changer. By augmenting existing prevention strategies with science-based artificial intelligence that uses an array of specialized machine learning techniques to spot attacker behaviors, regardless of the tools they’re using to pursue their objectives, cybersecurity teams can avail themselves of a reliable, low noise signal that alerts them of an attacker’s presence prior to the attacker achieving their desired objectives. At Vectra AI, we call this Attack Signal IntelligenceTM.
MOVEit Transfer Zero-Day Exploit Case Study
Exploiting CVE-2023-34363
Taking the MOVEit Transfer zero-day (CVE-2023-34363) as an example, the Cybersecurity & Infrastructure Security Agency (CISA) officially reported that the CL0P ransomware gang, aka TA505 was observed exploiting the vulnerability to place a “LEMURLOOT” web shell on the victim host to maintain persistence. The CISA report describes LEMURLOOT as having the following capabilities:
- Retrieve Microsoft Azure system settings, Azure Blob Storage, Azure Blob Storage account, Azure Blob key, and Azure Blob Container using the following query:
- Enumerate the underlying SQL database.
- Store a string sent by the operator and then retrieve a file with a name matching the string from the MOVEit Transfer system.
- Create a new administrator privileged account with a randomly generated username and LoginName and RealName values set to “Health Check Service.”
- Delete an account with LoginName and RealName values set to ‘Health Check Service.’
Limited Utility of Initial Access
While these capabilities are useful for establishing and maintaining persistence on the targeted host, they do not contribute significantly to achieving a more meaningful objective, such as coercing a ransom from the victim organization. Consequently, additional actions are necessary for the attacker to achieve their goals.
Note: there were observed instances of cl0p using a different zero-day for initial access without performing any follow-on actions in the target environment but it’s reasonable to conclude that the damage inflicted in those attacks was limited.
CISA Reports on CL0P's Toolset
CISA also reported CL0P’s use of a multitude of other tools that are purpose built for extending access in the victim environment:
- FlawedAmmyy/FlawedGrace Remote Access Trojan (RAT): Collects information and attempts to communicate with the Command and Control (C2) server to enable the download of additional malware components [T1071], [T1105].
- SDBot RAT: Propagates the infection, exploiting vulnerabilities and dropping copies of itself in removable drives and network shares [T1105]. It is also capable of propagating when shared though peer-to-peer (P2P) networks. SDBot is used as a backdoor [T1059.001] to enable other commands and functions to be executed in the compromised computer. This malware uses application shimming for persistence and to avoid detection [T1546.011].
- Truebot: A first-stage downloader module that can collect system information and take screenshots [T1113], developed and attributed to the Silence hacking group. After connecting to the C2 infrastructure, Truebot can be instructed to load shell code [T1055] or DLLs [T1574.002], download additional modules [T1129], run them, or delete itself [T1070]. In the case of TA505, Truebot has been used to download FlawedGrace or Cobalt Strike beacons.
- Cobalt Strike: Used to expand network access after gaining access to the Active Directory (AD) server [T1018].
Detecting and Monitoring the MOVEit Transfer Zero-Day with Vectra AI
All the tools described above share the common functionality of providing some measure of command and control to the target host. Vectra AI has several algorithms specifically designed to detect hidden tunnels, such as the Hidden HTTPS Tunnel algorithm, which can detect hidden tunnels in encrypted traffic without the need for doing any decryption of the HTTPS session.
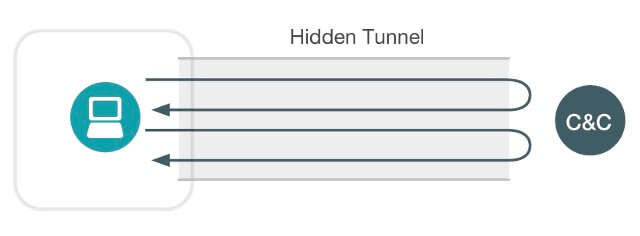
Vectra AI's Detection Triggers for Hidden Tunnels
- An internal host is communicating with an outside IP using HTTPS where another protocol is running over the top of the HTTPS sessions
- This represents a hidden tunnel involving one long session or multiple shorter sessions over a longer period of time mimicking normal encrypted Web traffic
- When it can be determined whether the tunneling software is console-based or driven via a graphical user interface, that indicator will be included in the detection
- The threat score is driven by the quantity of data sent via the tunnel
- The certainty score is driven by the combination of the persistence of the connections) and the degree to which the observed volume and timing of requests matches up with training samples
In addition to the command-and-control functionality, the SDBot Remote Access Trojan has the ability to self-propagate through the target environment by exploiting vulnerabilities. In such a scenario, Vectra AI’s Automated Replication algorithm will engage, enabling cybersecurity teams to identify “host zero” and follow the progression of the infection.
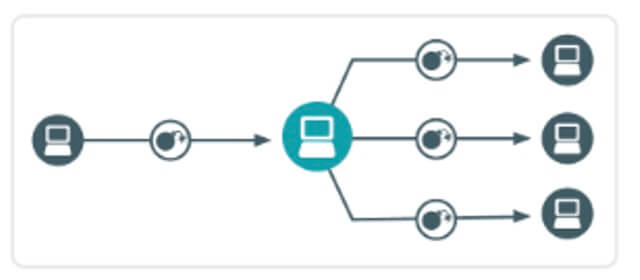
Vectra AI's Detection Triggers for Automated Replication
- An internal host is sending very similar payloads to several internal targets
- This may be the result of an infected host sending one or more exploits to other hosts in an attempt to infect them
- The certainty score is driven by the number of targeted hosts and the detection of an upstream propagator
- The threat score is driven by the number of targeted hosts and number of different exploits, particularly exploits on different ports
Transforming Zero-Day Threat Detection with AI
As outlined in the specific examples above, common attacker TTPs provide ample opportunity to detect the adversary’s presence prior to their desired objective being achieved. But opportunities do not automatically translate into results. The behaviors outlined can be difficult to detect with traditional signature-based solutions, especially when zero-day exploits are involved and other sources such as Windows Event Logs typically lack the context to distinguish between behaviors that are likely to be approved administrative actions versus ones that are unusual and potentially malicious.
When AI-based detection capabilities are deployed, the behaviors can be viewed through a different lens. “Does this HTTPS session exhibit a communication pattern that is indicative of external command and control?” That’s a question that can be answered with AI. “Would this WMI call further an attacker’s access through the environment and is it unusual for this host/user combination to make this WMI call?” These are also questions that can be answered with AI. “Is this payload transfer a one-off instance between two systems or does it resemble a broader pattern of payloads being pushed to many systems that is indicative of a worm spreading?” Again, a question that can be reliably answered with AI.
Conversely, trying to use AI (or any other threat detection technique for that matter) to detect the exploitation of a previously unknown vulnerability is, at present, not possible to do in a way that doesn’t generate a prohibitively large volume of data to analyze. Instead, by focusing on post-compromise attacker behaviors, we can produce a very reliable attack signal that is both low-noise and highly effective.
So rather than basing your zero-day strategy on the hope that you can patch before an attacker finds it, consider adapting your strategy to the assumed compromise mindset: There is very likely a zero-day vulnerability in our environment right now and if an attacker uses it to gain access to our network, we will be ready and able to detect their presence with AI-based post-compromise detection capabilities.
Exploring Vectra AI's Advanced Detection Capabilities
This is just a small sample of the AI-based detection algorithms built into Vectra AI’s Detect platform. For a more comprehensive review of detection capabilities, review the Understanding Vectra AI knowledgebase article and for a platform overview, start with our Attack Signal IntelligenceTM breakdown. If you’d like a personalized tour, reach out to your preferred technology partner for an introduction to our team.
--- References---
NIST
Microsoft
BlackFog
- The State of Ransomware 2020
- The State of Ransomware 2021
- The State of Ransomware 2022
- The State of Ransomware 2023
CISA
