INC Ransom
INC Ransom has been targeting critical infrastructure with sophisticated ransomware since 2023. It combines advanced intrusion techniques and extortion tactics, making it a serious threat to organizations worldwide. The group poses significant risks to organizations in sectors such as healthcare, manufacturing, government, and technology.

The origin of INC Ransom
INC Ransom is a sophisticated ransomware group that has emerged in August 2023. The group employs a methodical and multi-staged attack strategy, targeting vulnerable organizations with a combination of spear-phishing campaigns and exploitation of known vulnerabilities. Notably, the group has been linked to exploiting CVE-2023-3519, a critical flaw in Citrix NetScaler, to gain initial access. Their operations involve highly coordinated efforts to maximize the damage and enforce ransom payments, often leveraging "double extortion" tactics where stolen data is exfiltrated before being encrypted. INC Ransom is characterized by its ability to adapt, troubleshoot, and overcome technical challenges during attacks, indicating a well-organized and skilled operation.
While the specific individuals or groups behind INC Ransom are not publicly known, cybersecurity researchers believe Russian criminals are behind the operation.
Sources: SOCradar
Countries targeted by INC ransom
The group operates globally, with notable activity in North America, Europe, and parts of Asia. Countries such as the United States, the United Kingdom, Germany, and Australia have reported incidents attributed to INC Ransom. Their campaigns show no significant regional limitations, which indicates that their targeting is influenced by opportunity and potential financial gain rather than geopolitical motivations.

Industries targeted by INC ransom
INC Ransom is known for its broad targeting strategy, focusing on industries with critical infrastructure and low resilience to operational disruptions. Educational institutions, government organizations, manufacturers, retailers, energy and utility companies, and financial institutions have all been targeted. Most prominently, INC Ransom has gone after sensitive data in the healthcare sector, with damaging attacks on a children’s hospital in the UK and a health board in Scotland.

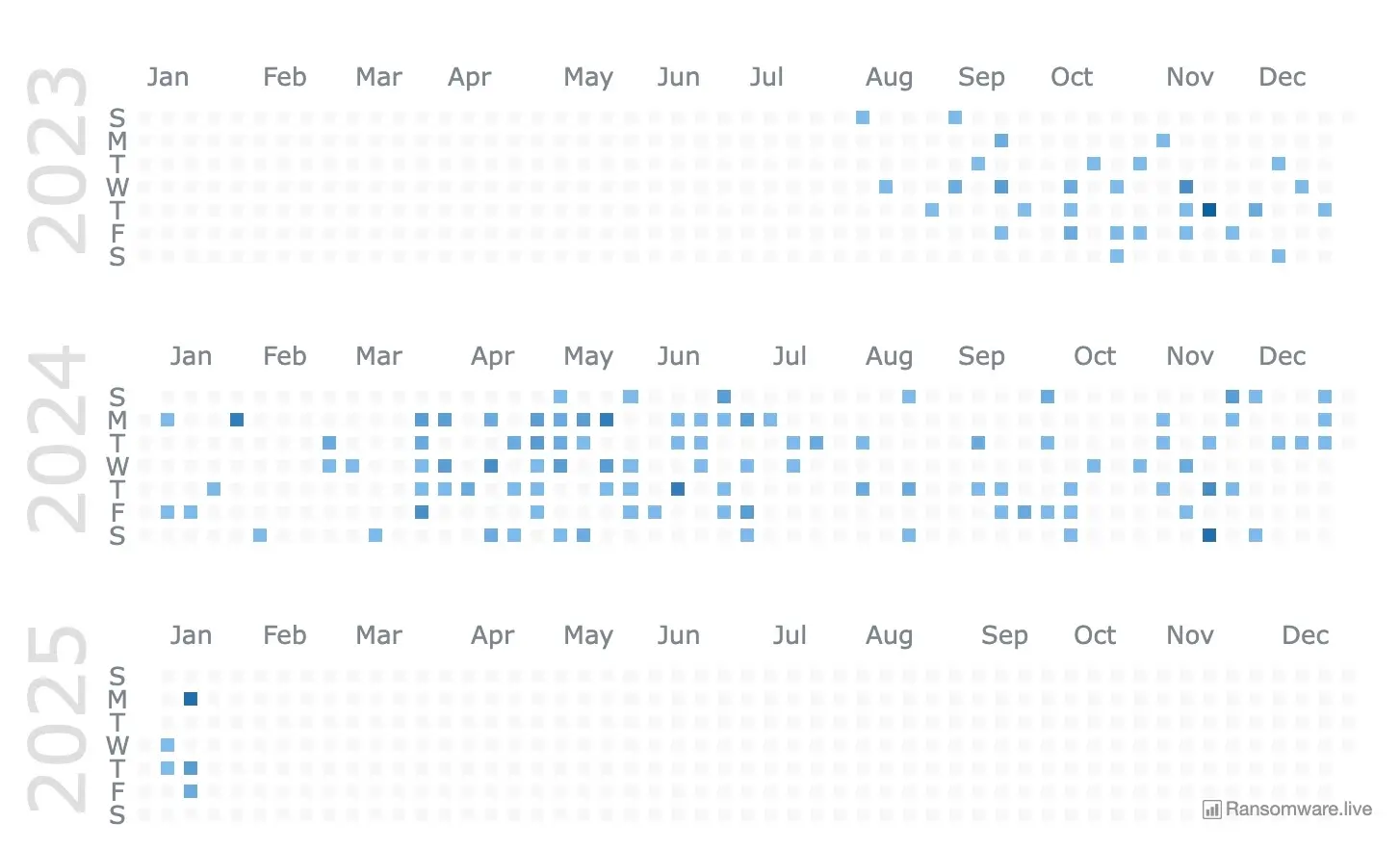
INC ransom's victims
An estimated 214 organizations have fallen prey to INC Ransom attacks. INC Ransom has been linked to high-profile attacks on hospital networks, municipal governments, and mid-sized enterprises. While specific victim names are often undisclosed, public reporting reveals a focus on organizations with weak cybersecurity defenses or those running outdated systems susceptible to exploitation.
INC Ransom attack method

Uses spear-phishing emails or exploits vulnerabilities in public-facing applications, such as CVE-2023-3519 in Citrix NetScaler.

Leverages tools like RDP to escalate privileges within the compromised system.

Employs obfuscated files, such as disguising PSExec as "winupd," to avoid detection.

Utilizes tools like Lsassy.py to dump credentials from memory.

Deploys tools like NETSCAN.EXE and Advanced IP Scanner for network reconnaissance to identify high-value targets.

Uses remote desktop software like AnyDesk.exe to move within the network.

Stages data using 7-Zip and MEGASync for exfiltration and encryption.

Runs encryption scripts using wmic.exe and disguised PSExec instances to initiate ransomware deployment.

Transfers stolen data for double extortion tactics using MEGASync or other cloud-based platforms.

Encrypts and/or destroys critical files, demanding ransom payments to restore access and prevent data leaks.

Uses spear-phishing emails or exploits vulnerabilities in public-facing applications, such as CVE-2023-3519 in Citrix NetScaler.

Leverages tools like RDP to escalate privileges within the compromised system.

Employs obfuscated files, such as disguising PSExec as "winupd," to avoid detection.

Utilizes tools like Lsassy.py to dump credentials from memory.

Deploys tools like NETSCAN.EXE and Advanced IP Scanner for network reconnaissance to identify high-value targets.

Uses remote desktop software like AnyDesk.exe to move within the network.

Stages data using 7-Zip and MEGASync for exfiltration and encryption.

Runs encryption scripts using wmic.exe and disguised PSExec instances to initiate ransomware deployment.

Transfers stolen data for double extortion tactics using MEGASync or other cloud-based platforms.

Encrypts and/or destroys critical files, demanding ransom payments to restore access and prevent data leaks.